The Jamtara scam is one of India’s most notorious cyber web crimes when a small district in the state of Jharkhand became the epicenter of phishing scams. It defrauds thousands of unsuspecting victims and manipulates youth gangs to obtain sensitive financial information. Including bank account details, OTP, and ATM PIN, used to identify yourself as a customer service officer. Bank officers or telecommunications executives Such scams cause huge financial losses across the country. And reveals gaps in India’s cyber security and law enforcement systems.
The Jamtara scam sheds light when it comes to insights into the size and scope of the entire network that goes into the scam. Many years have passed since its origin. India’s reputation for being called “Phishing capital” is accused of victimizing the masses In this article, we will explain the origins, directions, effects, and lessons behind such shocking cases of Cybercrime:
What is the Jamtara Scam About?
The Jamtara scam involves a phishing scam. Where scammers trick victims into providing personal and financial information through phone calls. In general, These scammers target the general public. Including the elderly, housewives, and villagers, such people are generally easy targets for cyber fraudsters.
How Did the Jamtara Scam Begin?
The scam was started by a group of tech-savvy youths from Jharkhand’s Jamtara district who understood the potential of phishing as a way to make quick money. They started calling people claiming to be officials of a bank or telecommunications company. And asking for confidential details pretenses When they catch those details They will drain victims’ bank accounts or conduct unauthorized transactions online.
How Did it Proceed?
Scammers use a useful but powerful trick:
- Unscheduled Calls: They will call random people. Everywhere in the country Claiming to represent reputable organizations such as banks, telecommunications companies E-commerce companies.
- Fake situations: They create false situations, such as deactivating a bank account or SIM card. And said they wanted the same activation details.
- Sensitive information: They ask for sensitive information such as debit/credit card numbers, CVVcodese, ATPINsIN, or OTP to authenticate the victim’s account.
- Unauthorized transactions: They will engage in unauthorized transactions with such information. Withdraw cash from the victim’s account or even buy products online…
Scams are starting to get organized where fraudsters keep records of their calls. Including the victim’s name Telephone number and financial information, makes it easier to target more people.
How 6 Men in Jamtara Defrauded 2,500 People ?
Six young men from Jamtara fooled 2,500 people by claiming to be customer service officers. The scam, which started with Jamtara, began when law enforcement agencies learned that six men from Jamtara were phishing and luring over 2,500 people. They were able to impersonate customer service representatives and reveal confidential information to the victims. The roles of six men were young people in their early 20s with limited formal education but skilled in using technology. They take advantage of the lack of cyber awareness among the general population to carry out scams. Despite its origins in a small town, they were able to create a highly efficient phishing system.
How Do Scammers Work?
Fraudsters use the simplest tools to do their job: cell phones. More than one SIM card and caller ID spoofing apps This section provides detailed information about the strategy:
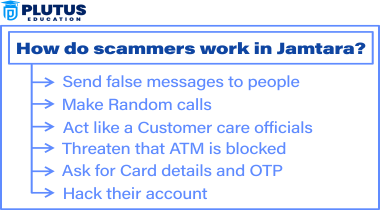
- Caller ID Spoofing: They have an app source to display fake caller IDs. Therefore, it appears that the call is coming from an official source, such as a bank or telecommunications company.
- Persuasive Communication: They use jargon and a professional customer service tone to make it easier for victims to trust them. Capitalize on fear and urgency: They create situations that make the victim feel pressured to take immediate action, such as “If you don’t check your details, Your bank account will be frozen.
- Multiple Calls: If the victim refuses to share information during the first call. The perpetrators will call again and again until they gather the necessary information results of one’s actions These six people did not act alone. But these actions truly created the phishing ecosystem in Jamtara. These successes have led hundreds of young people in the district to become C.S.
The Rise of Cybercrime in Jamtara
The small scam project of Jamtara expanded to become the largest phishing network and even earned it the title “India’s phishing capital.”
Why Jamtara?
Several factors contributed to cybercrime:
- Lack of Jobs: Young people who have fewer opportunities for formal jobs resort to phishing as an easy way to do a little money.
- Availability of Technology: Cheap mobile phones and internet connections provided the scammers with the tools they needed to operate.
- Absence of Awareness: Victims all over the country lacked awareness about phishing scams, making them easy targets.
- Weak Law Enforcement: In the early years, law enforcement agencies lacked the expertise to track and apprehend cybercriminals.
How has Management Reacted to Jamtara Scam?
Jamtara scams have increased the efforts of the authorities in fighting cyber crimes. Year after year, many activities are being carried out on Jamtara to eradicate net phishing. Law enforcement actions
- Police operations:: Police forces carried out several raids in Jamtara. Hundreds of people were arrested. And seized mobile phones, SIM cards, and other evidence Related…
- Interstate coordination:: Police forces from various states are involved in tracking down and arresting these scammers.
- Tracking financial transactions: Banks and police monitor suspicious transactions to look for patterns of fraud.
Measures to Prevent Cybercrime
Government and law enforcement agencies have taken several steps to combat phishing scams:
- Cyber Awareness Program: Educate people about phishing and how not to fall prey to such scams.
- Tougher laws: Impose harsher penalties for cyber crimes under the IT Act.
- Cyber Crime Helpline: A nationwide hotline has been launched to report online fraud.
The Psychological Tactics Behind the Jamtara Scam
The success of the Jamtara scam did not solely rely on technology. It was greatly based on psychological manipulation. Scammers understand human psychology and how to use it to their advantage. They came up with scenarios that instill fear, a sense of urgency, or a feeling of trust in their victims, which is why they easily receive sensitive information from them.
Fear and Urgency
The scammers often told victims that their bank accounts or SIM cards would be deactivated if they did not act immediately. This sense of urgency caused panic, making victims more susceptible to manipulation.
Building Trust
The fraudsters spoke in polite and professional tones, used industry jargon, and even shared partial details of the victim’s account (obtained from leaked databases) to build trust. This made the victims believe they were speaking to legitimate officials.
Exploiting Ignorance
Many victims had no idea how dangerous it is to share the OTPs of their cards or ATM PINs over the phone. The scammers took advantage of their ignorance and thus succeeded in tricking them to give away some critical information. Knowing these techniques is important to make people aware of cybercrime prevention.
The Media Role in Unveiling the Jamtara Scam
Mostly, it was media coverage that catapulted the scam to a national scale, therefore, it was for this reason that the magnitude of the phishing network was first exposed and awareness is drawn.
News reports and documentaries
Major news platforms were reporting about the scam in the year 2018 that reached the public eye. Documentaries and investigative pieces have come out showing how the phishing networks work who the scammers are, and which victims they target as well.
The Role of Entertainment
Another significant factor that led to the amplification of the problem of cybercrime in India was the Netflix series Jamtara: Sabka Number Ayega. This show was inspired by true events and demonstrated how young men from Jamtara used technology and psychological tactics to run a phishing racket. It not only entertained audiences but also educated them about phishing scams and the need for caution.
Awareness Campaigns Triggered by Media
After media houses and entertainment released their reports regarding this scam, the banks, telephone companies, and other law agencies made public the education campaigns concerning people’s protection of the details and identity recognition of phishes.
Leaning on mass media, therefore, authorities were in a better position to deliver this message to larger proportions of populations that would discourage other scams to arise in the future.
Lessons from the Jamtara scam
The Jamtara scandal provides important lessons for individuals, businesses, and policymakers:
1. Awareness is Important
People need to be educated about the dangers of sharing sensitive information over the phone or online. Cyber awareness programs should target vulnerable groups such as the elderly and rural populations.
2. Strengthen Cyber Security
Organizations need to spend more on better security systems to protect customer data. Banks and telecommunications companies constantly scan their systems for signs of fraud.
3. Employment Opportunities
Districts like Jamtara will reduce unemployment and eliminate the attraction of cyber crimes. Vocational training programs can be a livelihood option.
Jamtara Scam FAQs
Q1. What is the Jamtara scam?
The Jamtara scam is a phishing racket that originated in Jamtara, Jharkhand. TScammers were posing as customer care executives from which sensitive information and money of people all over India were stolen.
Q2. How many people were affected by the Jamtara scam?
More than 2,500 people have been confirmed victims of the scam, but the number is suspected to be much higher. The financial losses are in crores of rupees.
Q3. How do Jamtara scammers work?
The scammers call the victim under the guise of banks or telecom companies, create some kind of fake emergency, and convince the victim to share their confidential details such as OTPs and PINs.
Q4. What measures are being taken to stop the Jamtara scam?
Authorities have conducted raids, arrested hundreds of scammers, and launched public awareness campaigns. Cybercrime laws have also been strengthened.
Q5. How can I protect myself from phishing scams?
Never share sensitive information like OTPs or ATM PINs over the phone. Verify the identity of callers, and report suspicious calls to the cybercrime helpline.



